BUUOJ 加固题 WP
Ezsql
打开 /var/www/html/index.php,发现没有做任何的过滤,明显的 SQL 注入:
<?php
error_reporting(0);
include 'dbConnect.php';
$username = $_GET['username'];
$password = $_GET['password'];
if (isset($_GET['username']) && isset($_GET['password'])) {
$sql = "SELECT * FROM users WHERE username = '$username' AND password = '$password'";
$result = $mysqli->query($sql);
if (!$result)
die(mysqli_error($mysqli));
$data = $result->fetch_all(); // 从结果集中获取所有数据
if (!empty($data)) {
echo '登录成功!';
} else {
echo "用户名或密码错误";
}
}
?>因此用SQL预处理语句防护就可以了。这里偷懒了,直接限定用户名密码必须是字母+数字就可以了。
直接过滤非字母数字
if (preg_match('/^[a-zA-Z0-9]+$/', $username) && preg_match('/^[a-zA-Z0-9]+$/', $password)) { }mysqli预处理
$stmt = $mysqli->prepare("SELECT * FROM users WHERE username = ? AND password = ?");
$stmt->bind_param("ss", $username, $password);
$stmt->execute();
$result = $stmt->get_result();
if ($result->num_rows > 0) {
echo '登录成功!';
} else {
echo "用户名或密码错误";
}
$stmt->close();PDO预处理
$stmt = $pdo->prepare("SELECT * FROM users WHERE username = :username AND password = :password");
$stmt->bindParam(':username', $username);
$stmt->bindParam(':password', $password);
$stmt->execute();
if ($stmt->rowCount() > 0) {
echo '登录成功!';
} else {
echo "用户名或密码错误";
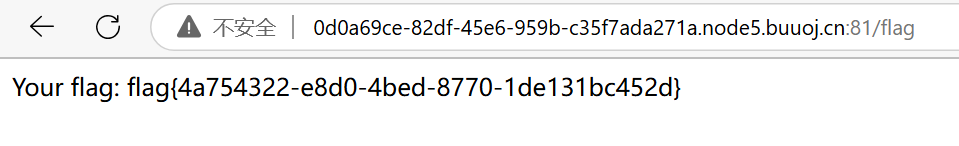
}成功拿到flag:
持续更新中……
Comments